License Plate Image Recognition
In the case of security footage, the images of the vehicle are often grainy and skewed to begin with and then are stored in low quality. Here normal OCR algorithms fail. This research effort is to see if addling localization algorithms, that is having a machine learning algorithm say where a license plate is, increases the accuracy of “out of the box” OCR algorithms. After verifying the effectiveness of the localization algorithm, curricular training will be used to retrain the localization model on increasingly degraded images. The OCR algorithm will also be retrained in a similar way. This will then extend into a semi-truck data set. Where instead of looking for vehicle license plates, the localization algorithm will be retrained on the identification numbers found on the side of semi-trucks. The same processes of curricular training will also be applied to this data set.

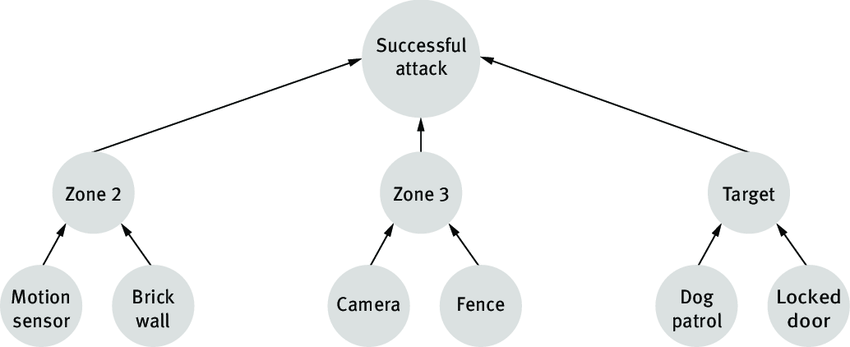
Intrusion Prediction Model using Dynamic Attack Tree
Our research goal is to develop an attack prediction model based on the alert information generated by the intrusion detection system. The prediction model will use the concept of attack tree, a powerful approach of modeling the security vulnerabilities of information systems. This structure is organized as a tree, where the elementary attacks are placed at the leaf level and the primary attack is placed at the root. In the top-down approach, the internal nodes are considered as a refinement of the higher-level nodes. We prefer attack tree over attack graph as attack trees are architecturally more rigorous and provide more insights regarding attack scenarios.
Using Isochrones to Understand Traffic Congestion
In a cross department research effort, one of the many projects being developed is an isochrone algorithm for using Google Maps API's to pull travel time data. For any given location, we can represent the distance we are able to travel in some given time period as an isochrone. These can be used for a wide variety of purposes, but ultimately represent a visualization of traffic congestion over a given day.
Wireless Cluster Computers using Mesh Networks
The goal of this research is to be able to easily add nodes to a cluster to increase its computing power and in the event that one of the nodes gets taken down, the rest of the cluster will continue its operations.